Data security is reinventing itself. As new data security posture management solutions come to market, organizations are increasingly recognizing the opportunity to provide evidence-based security that proves how their data is being protected. But what exactly is data security posture, and how do you manage it?
Data security posture management (DSPM) became mainstream following the publication of Gartner® Cool Vendors™ in Data Security—Secure and Accelerate Advanced Use Cases. In that report, Gartner1 seems to have kicked off the popular use of the data security posture management term and massive investment in this space by every VC. Since that report, Gartner has identified at least 16 DSPM vendors, including Symmetry Systems.
What is Data Security Posture?
There certainly is a lot being marketed and published about data security posture management solutions themselves, but we first wanted to dig into what is data security posture?
Symmetry Systems defines data security posture as “…the current status of the capabilities required to protect data from unauthorized access, destruction, and/or alteration. Data security posture is an assessment of an organization’s data store or individual data objects:
Data attack surface: A mapping of the data to the identities, vulnerabilities, and other misconfigurations that can be used as entry points to gain access to it.
Data security control effectiveness: An evidence-based assessment of the data security and privacy controls against industry best practices and organizational policy.
Data blast radius: A quantifiable assessment of the data at risk or the maximum potential impact of a security breach of a single identity, data store, vulnerability, or misconfiguration. This includes identifying the types and volumes of data that could be affected, as well as the estimated costs and predicted consequences based on current control effectiveness.
Overall, a robust organizational data security posture involves a comprehensive approach to managing the security of an organization’s data, including continuous inventory and classification of data, ongoing assessment and improvement of data security controls, proactive rightsizing of access to data, and a commitment to continuous monitoring and response to unusual usage of data.”
To maintain a good data security posture, organizations should do the following:
Inventory your data: A data inventory—that is a comprehensive list of all data stores and the sensitivity of the data within them—is an essential first step in determining the current status of capabilities.
Monitor data activity and data flows: An important next step is to ensure you have visibility into activity and the flow of your data, because it improves your ability to detect and respond to any anomalies or indicators of compromise as you improve your data security posture.
Assess data security controls: Once you have this visibility and insight into your data, you can conduct an evidence-based assessment of your data security controls. This should include determining the level of encryption of the data, the validity of hashing and tokenization of data in certain environments, and most importantly the validation of cloud configurations and access controls, including authentication required to access data.
Reduce data attack surface: Organizations should have processes in place to use the results of this analysis to proactively identify and reduce the data attack surface. This should include ensuring multi-factor authentication is required for all identities with access to sensitive data and data stores that contain sensitive data and removing dormant accounts from the environment.
Minimize blast radius: Organizations must constantly assess the volume of data at risk and prioritize pragmatic steps to minimize the potential impact of a security breach of a single identity, data store, vulnerability, or misconfiguration. This should include removing sensitive data from inappropriate environments, identifying, and eliminating misconfigurations, and data minimization by archiving or deleting data or by deleting unused privileges from active accounts.
The Symmetry DataGuard Solution
Symmetry DataGuard is a purpose-built data security posture management platform. Symmetry DataGuard doesn’t simply augment existing SaaS platforms with data classification to claim DSPM coverage; instead, it was designed from the ground up to maximize the protection of data. The platform is typically deployed within the customer’s cloud environment as a way to ensure that data never leaves the customer’s control. This deployment model is well suited for dealing with data, regardless of sensitivity and various compliance regulations.
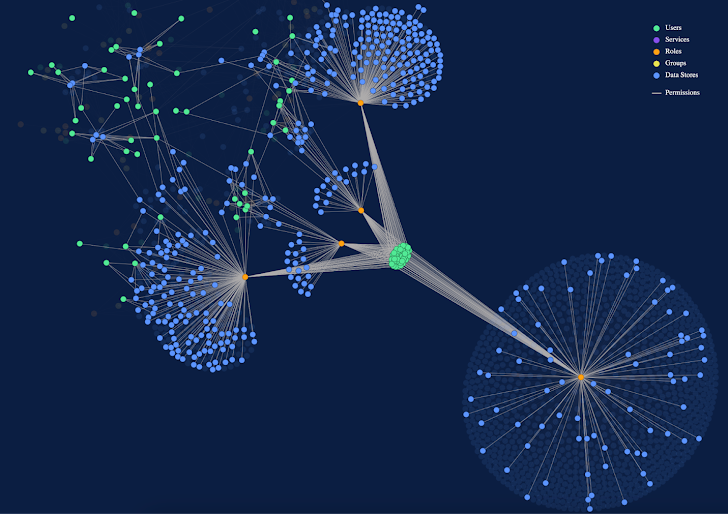
At its core, the Symmetry DataGuard platform has a deep graph of data objects, identities, and all permissions to and actions that are performed on the data objects. This interconnected graph is used to provide the elements needed for organizations to manage their data security posture. We reviewed the Symmetry Solution to see how it helps organizations address a few key areas.
Data Inventory
Once installed and configured, Symmetry DataGuard gathers information from the cloud environments. This is made easier by installing within the customer’s cloud environment, but as long as Symmetry DataGuard has appropriate permissions to query the data, it can aggregate information across your cloud environments. To avoid unnecessary data egress fees, Symmetry Systems recommends deploying Symmetry DataGuard in each cloud environment (i.e., AWS, Azure, etc.). Agentless discovery quickly collects information about:
- The cloud environment.
- The identities (including users, services, roles, and groups) with access to the environment.
- The datastores within the environment.
Monitor Data Activity and Data Flows
As part of the discovery and ongoing monitoring of the environment, Symmetry DataGuard collects telemetry on all the data activity or data operations being performed on data within your environment. This includes failed and denied attempts. This telemetry is used to deepen the insight provided on who is accessing an organization’s data and where that data is flowing to or from as a result.
This information is cross-correlated with the data inventory to help organizations pinpoint external data flows, failed attempts to access sensitive data, and a number of other interesting data-centric threat detection scenarios.
Operations are grouped into four high-level classes: creation, read, update, or deletion of data. This helps when prioritizing unusual or high-risk activity against specific data.
Perform Assessment of Data Security Controls
Symmetry DataGuard also assesses the data security and identity configurations and can raise alerts when configurations fail to meet defined policies or are changed. These configurations include, but are not limited to, determining whether:
- Data is encrypted. (This includes native.)
- MFA is enabled.
- Monitoring is enabled.
Symmetry DataGuard has out-of-the-box compliance policies that are used to check for compliance with data-centric portions of the Center of Internet Security (CIS) benchmarks and other compliance frameworks.
The Takeaway
A good data security posture reduces the attack surface and blast radius of your organization’s data. Achieving and maintaining a good data security posture requires a detailed understanding of the data itself, the identities that can access it, the controls that protect it and monitoring of the operations being performed. A leading platform like Symmetry DataGuard is able to maintain data inventory, monitor operations and activity and check for secure data security configuration and compliance, and thereby provide evidence-based data security.
Credit : Hackers News
15
JunRecent Blog
Quantum Gravity Gradiometer PathFinderApr 28, 2025
The TechKriti 2025Apr 26, 2025
India’s First Quantum Computing VillageApr 24, 2025
India’s Achievement In QKDApr 22, 2025
The V2G TechnologyApr 21, 2025