Cybersecurity or Information Security threats are at an unequaled high. 1,862 data breaches occurred in the previous year, up over 68% from 2020. A concentrate by Duke College found that over 80% of U.S firms have encountered a hack. However, 23% of organizations in the U.S. have not put resources into cybersecurity. That doesn’t make any sense! An association wide cybersecurity risk management plan is the best method for safeguarding against cyberattacks. Whether or not your business feels it’s vital right now, it never feels fundamental until it’s past the point of no return. Furthermore, it’s more affordable to put resources into a proactive arrangement than to deal with the results of a breach.
A single breach can set an organization back $4.35 million USD. In addition to financial losses, organizations also suffer data loss, compromised credentials, and reputational damages. Can you imagine a customer falling victim to identity theft because your organization was hacked? You can consider your client-business relationship terminated. In fact, research shows that 1 in 4 Americans will stop business with a company that has been breached. Additionally, 2 in 3 people lose trust in breached businesses.
There are endless reasons for your organization to create an effective cybersecurity risk management plan, and it’s not as complex as you may think. Follow along to learn how to create an effective cybersecurity risk management plan and implement it within your organization.
What is a Information security Risk Management Plan?
A cybersecurity risk management plan is a strategic approach to prioritizing threats. It is an ongoing process of identifying, analyzing, evaluating, and addressing cybersecurity threats within your organization. The main objective is to proactively identify and manage critical threats to prevent data breaches and prioritize protecting clients’ personal information.
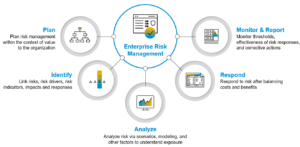
The cybersecurity risk management process involves four primary stages:
- Risk Identification – Identifying current and potential threats that may affect your organization’s cybersecurity infrastructure and business operations.
- Risk Assessment – Analyzing the identified risks to determine their priority levels (i.e., low risk to critical risk) and their potential impact.
- Risk Treatment – Breaking down the methods, procedures, and technologies necessary to address the analyzed risks.
- Risk Monitoring and Reporting – Reporting on risk findings and effectiveness of mitigation efforts, and consistently monitoring and adjusting the management plan as needed.
Cybersecurity risk management is an ongoing process, not a one-and-done. Based on the findings from consistent monitoring and reporting, organizations can continue to adjust and configure new risk mitigation efforts as seen fit.
Is Cybersecurity only for CIOs and IT?
An effective plan is sustained through the actions of all employees of an organization, technical and non-technical staff included. Many organizations believe cybersecurity is in the hands of IT and CIOs, however, that logic is flawed. Cybersecurity threats can target members at every level of an organization. If an employee does not have the necessary knowledge or formal training in place to navigate threats, it can result in breaches and serious consequences for organizations.
Annual statistics demonstrate the importance of employee training and participation in cybersecurity risk management plans. As of 2022, phishing schemes have become the #1 threat to cybersecurity. Phishing schemes work by tricking employees, usually via email, into divulging important and/or confidential information by impersonating well-known people. A study by IBM surveyed employees across multiple industries and found that 97% were unable to recognize a sophisticated phishing scheme. Even more interesting, 95% of cybersecurity breaches are a result of human error, either intentional or unintentional. Both of these troubling statistics can be lowered with proper cybersecurity training.
These statistics highlight the importance of cybersecurity training for employees respective to the security of your organization. Every member of an organization is a key player in the success of a cybersecurity risk management plan and should be formulated into the plan accordingly.
Now, let’s dive into how to create an effective plan:
Information Security Risk Management Framework
There are several cybersecurity risk management frameworks that exist to provide set standards of security for leaders and organizations across the world. Organizations that are compliant with these standards exemplify their ability to meet the security requirements necessary to operate a business and protect clients’ information. The most common frameworks include:
- ISO 27001 – The leading international standard for protecting and managing information security within an organization. This framework includes a combination of policies and procedures which revolve around three objectives; 1. confidentiality (only authorized entities are granted access to sensitive information), 2. integrity (only enabling authorized users to modify sensitive information) and 3. availability (sensitive information is accessible to authorized entities only)
- SOC 2 Type 2 – The globally recognized Service Organization Control (SOC) audit evaluates and reports on how cloud-based service providers manage sensitive information. SOC 2 Type 2 evaluates service providers based on five key organizational controls: 1. security (how protected information systems are), 2. availability (information is readily available for authorized use), 3. processing integrity (data processing is complete, valid, accurate, timely, and authorized), 4. confidentiality (information is kept secure), 5. privacy (PII is securely collected, processed, stored, and disposed of).
- HIPAA – The Health Insurance Portability and Accountability Act was created to protect patient’s personal information in the United States. Organizations that are compliant with HIPAA agree to safeguard PHI from unwarranted disclosure and give patients’ rights to access their documentation.
How to Create an Effective Information Security Risk Management Plan
Creating an effective cybersecurity risk management plan for your organization involves many moving parts. A combination of the above-mentioned strategies and frameworks can provide an efficient and secure foundation for creating your plan.
Step 1: Create a cybersecurity team
First, we recommend your business create a cybersecurity team that is dedicated to fostering cybersecurity awareness within the organization, providing training, and setting security procedures and rules in place. Creating a cybersecurity team ensures that cybersecurity risk management is consistently managed and prioritized so that nothing falls between the cracks.
Step 2: Develop a cybersecurity training plan
Secondly, your cybersecurity team should create a cybersecurity training plan at the organizational level. All employees should routinely be evaluated and briefed on cybersecurity best practices, risks, and tools for de-escalating threats. A digital security course and/or hiring a cybersecurity expert to teach employees is a great start.
Step 3: Implement the four primary stages of a cybersecurity risk management plan
Now that the foundation is built, your company should implement the “four stages of a cybersecurity risk management process” mentioned at the beginning of the article. Your organization should identify current and potential risks to your security infrastructure, assess the identified risks and prioritize them based on the projected effect on business operations, treat the risks with appropriate tools, and monitor and report on findings.
*The four stages can be implemented concurrently with employee cybersecurity training.
Step 4: Obtain security standard certifications
Security certifications create an advantage for your organization not only in regards to security but also in reputation. Businesses that possess security certifications, such as ISO 27001, SOC 2 Type 2 and HIPAA, exemplify their ability to safeguard client data. This is seen as positive in the eye of current and prospective clients. Although these certifications can be time-consuming and costly, they are an important component of an effective cybersecurity risk management plan.
For small-medium businesses and companies that cannot afford to allocate a large budget to cybersecurity risk management- Using cloud-based solutions that are compliant with essential security standards is a great alternative.
Blog By: Priyanka Rana

10
MarInformation Security Risk Management Plan
Mar 10, 2023Recent Blog
When Monuments Delisted !!Apr 08, 2025
The Frontier Technologies Readiness IndexApr 07, 2025
Vikram 3201 & Kalpana 3201Apr 04, 2025
The Open Weight Language ModelApr 03, 2025
Asia Cup 2025Apr 02, 2025