Domain Name Server- DNS and It’s Working
Blog Credit: Trupti Thakur
Image Courtesy: Google
Domain Name Server is a prominent building block of the Internet. It’s developed as a system to convert alphabetical names into IP addresses, allowing users to access websites and exchange e-mails. DNS is organized into a tree-like infrastructure where the first level contains the topmost domains, such as .com and .org. The second-level nodes contain general, traditional domain names. The ‘leaf’ nodes on this tree are known as hosts.
DNS works similarly to a database that is accessed by millions of computer systems in trying to identify which address is most likely to solve a user’s query.
In DNS attacks, hackers will sometimes target the servers which contain the domain names. In other cases, these attackers will try to determine vulnerabilities within the system itself and exploit them for their own good.
Types of Attacks:
- Denial of service (DoS): An attack where the attacker renders a computer useless (inaccessible) to the user by making a resource unavailable or by flooding the system with traffic.
- Distributed denial of service (DDoS): The attacker controls an overwhelming amount of computers (hundreds or thousands) in order to spread malware and flood the victim’s computer with unnecessary and overloading traffic. Eventually, unable to harness the power necessary to handle the intensive processing, the systems will overload and crash.
- DNS spoofing (also known as DNS cache poisoning): An attacker will drive the traffic away from real DNS servers and redirect them to a “pirate” server, unbeknownst to the users. This may cause the corruption/theft of a user’s personal data.
- Fast flux: An attacker will typically spoof his IP address while performing an attack. Fast flux is a technique to constantly change location-based data to hide where the attack is coming from. This will mask the attacker’s real location, giving him the time needed to exploit the attack. Flux can be single or double or of any other variant. A single flux changes the address of the web server while double flux changes both the address of the web server and the names of DNS serves.
- Reflected attacks: Attackers will send thousands of queries while spoofing their own IP address and using the victim’s source address. When these queries are answered, they will all be redirected to the victim himself.
- Reflective amplification DoS: When the size of the answer is considerably larger than the query itself, a flux is triggered, causing an amplification effect. This generally uses the same method as a reflected attack, but this attack will overwhelm the user’s system’s infrastructure further.
Measures against DNS attacks:
- Use digital signatures and certificates to authenticate sessions in order to protect private data.
- Update regularly and use the latest software versions, such as BIND. BIND is open-source software that resolves DNS queries for users. It is widely used by a good majority of the DNS servers on the Internet.
- Install appropriate patches and fix faulty bugs regularly.
- Replicate data in a few other servers, so that if data is corrupted/lost in one server, it can be recovered from the others. This could also prevent single-point failure.
- Block redundant queries in order to prevent spoofing.
- Limit the number of possible queries.
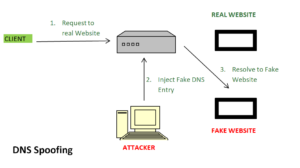
DNS Spoofing means getting the wrong entry or IP address of the requested site from the DNS server. Attackers find out flaws in the DNS system and take control and will redirect to a malicious website.
In above image –
- Request to Real Website: User hits a request for a particular website it goes to the DNS server to resolve the IP address of that website.
- Inject Fake DNS entry: Hackers already take control over the DNS server by detecting the flaws and now they add false entries to the DNS server.
- Resolve to Fake Website: Since the fake entry in the DNS server redirect the user to the wrong website.
To Prevent From DNS Spoofing –
- DNS Security Extensions (DNSSEC) is used to add an additional layer of security in the DNS resolution process to prevent security threats such as DNS Spoofing or DNS cache poisoning.
- DNSSEC protects against such attacks by digitally ‘signing’ data so you can be assured it is valid.
- Implement Source Authentication:Source authentication can be used to verify that the source of the DNS request is legitimate. This can be achieved using techniques such as IPsec or TLS to authenticate the requestor and ensure that the request has not been tampered with in transit.
- Use Response Rate Limiting:Response Rate Limiting (RRL) is a technique that limits the rate at which a DNS server responds to queries. This can help prevent DNS amplification attacks by reducing the number of responses that can be generated by a single query.
- Implement DNS Filtering:DNS filtering can be used to block traffic to known malicious domains or IP addresses. This can be done using DNS blacklists or whitelists that are regularly updated with known malicious or legitimate domains.
- Use DNS Monitoring and Analysis: DNS monitoring and analysis can be used to detect anomalies in DNS traffic that may indicate a DNS spoofing attack. This can be achieved using techniques such as packet capture and analysis, log analysis, or real-time monitoring of DNS traffic.
- Regularly Update DNS Software and Patches:Regularly updating DNS software and patches can help prevent known vulnerabilities from being exploited by attackers. This can be achieved by regularly checking for updates and patches from the vendor or using automated patch management tools.
Conclusion: DNS attacks can have serious consequences, but with the right security measures in place, it is possible to mitigate the risk of these attacks. By staying informed about the latest threats and vulnerabilities and implementing best practices for DNS security, you can help protect your organization from these types of attacks.
Blog By: Trupti Thakur

10
JunDomain Name Server And The Working
Jun 10, 2023Recent Blog
Quantum Gravity Gradiometer PathFinderApr 28, 2025
The TechKriti 2025Apr 26, 2025
India’s First Quantum Computing VillageApr 24, 2025
India’s Achievement In QKDApr 22, 2025
The V2G TechnologyApr 21, 2025