How We Can Protect Our Personal Data Online
- Mar 16, 2023
In 2022, more than 1.5 million U.S. online clients had their own data compromised. A large number of these clients became victims of data fraud and experienced a misfortune in individual budgets and also the headaches from being required to manage the fallout. Despite the fact that cyberattacks have expanded dramatically throughout the course […]
Space X- Falcon 9 rocket
- Mar 16, 2023
Falcon 9 Rocket Blog Credit: Trupti Thakur Image Courtesy: Google SpaceX launched a Falcon 9 rocket from Cape Canaveral Space Force Station with 40 more internet satellites for rival OneWeb, followed by the landing of the rocket’s first stage booster back at the Florida spaceport. More About the SpaceX launch: […]
How SMBs Can Improve Their Security
- Mar 14, 2023
If somebody somehow happened to ask you who is impacted by security breaches the most, odds are good that your most memorable idea would be of large organizations. Maybe organizations like Yahoo or Facebook ring a bell – organizations that are immense and hold untold measures of confidential data. While accounts of global breaches frequently […]
Electro Fuels
- Mar 14, 2023
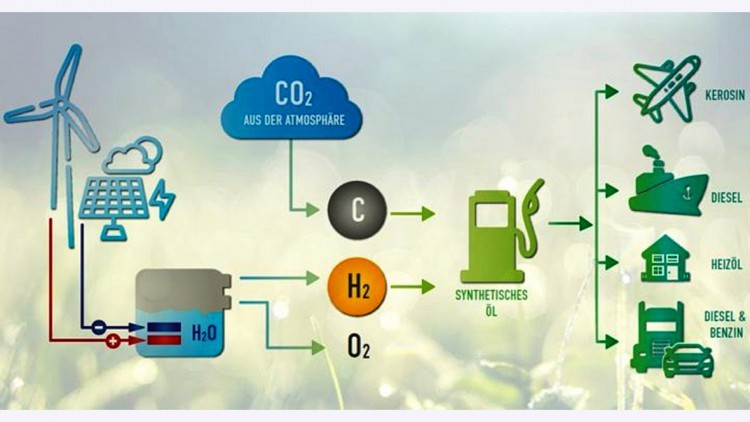
Electro Fuels (E-Fuels) Blog Credit: Trupti Thakur Image Courtesy: Google E-fuels are a type of fuel […]
Introduction With Bionic Eye
- Mar 13, 2023
Bionic Eye Blog Credit: Trupti Thakur Image Courtesy: Google Bionics or biologically inspired engineering is the application of biological methods and systems found in nature to the study and design of engineering systems and modern technology. The bionic eye consists of a retinal implant connected to a video camera that […]
Importance of Data Backup
- Mar 11, 2023
Introduction When was the last time you backed up your data? Today? Yesterday? A week ago? A month ago? So long that you’ve forgotten? As a business, it’s important to back up your data to prevent data loss and make recovery quicker. In fact, experts recommend the average mid-size company should backup data every 24 hours. […]
H3N2 Virus In India
- Mar 11, 2023
H3N2 Virus In India Blog Credit: Trupti Thakur Image Courtesy: Google According to WHO, H3N2 is a subtype of Influenza A virus which majorly affects humans. Here are the sympoms of H3N2 influenza you should not ignore. A sharp rise in H3N2 influenza cases has been reported in India. […]
Information Security Risk Management Plan
- Mar 10, 2023
Cybersecurity or Information Security threats are at an unequaled high. 1,862 data breaches occurred in the previous year, up over 68% from 2020. A concentrate by Duke College found that over 80% of U.S firms have encountered a hack. However, 23% of organizations in the U.S. have not put resources into cybersecurity. That doesn’t make […]
Green Hydrogen In India
- Mar 10, 2023
Green Hydrogen In India Blog Credit: Trupti Thakur Image Courtesy: Google Green hydrogen is hydrogen produced by splitting water by electrolysis. This produces only hydrogen and oxygen. We can use the hydrogen and vent the oxygen to the atmosphere with no negative impact. To achieve the electrolysis we need electricity, we need power. Also […]
22 Safest Practices for Protecting Data Privacy in 2023
- Mar 09, 2023
Data Security Safest and Best Practices The current geopolitical climate has created a frenzy amongst online users regarding the safety of their online data. Currently, the U.S. Government warns of potential malicious cyber activity from opposing countries. In 2021, there were over 500 million cyberattacks with many resulting in breaches, data loss, and reputational damage. With cyberattacks on the […]
Security Incident In The Organization
- Mar 09, 2023
Security Incident in Any Organization Blog Credit: Trupti Thakur Image Courtesy: Google A security incident can be anything from an active threat to an attempted intrusion to a successful compromise or data breach. Policy violations and unauthorized access to data such as health, financial, social security numbers, and personally identifiable records are all examples of security […]
KEY to HIPAA Compliance
- Mar 06, 2023
HIPAA, or the Health Insurance Portability and Accountability Act, is a federal law that outlines the requirements for protecting sensitive patient information, also known as Protected Health Information (PHI). HIPAA compliance is mandatory for healthcare organizations, such as hospitals, clinics, and health plans, as well as for business associates that handle PHI on behalf […]