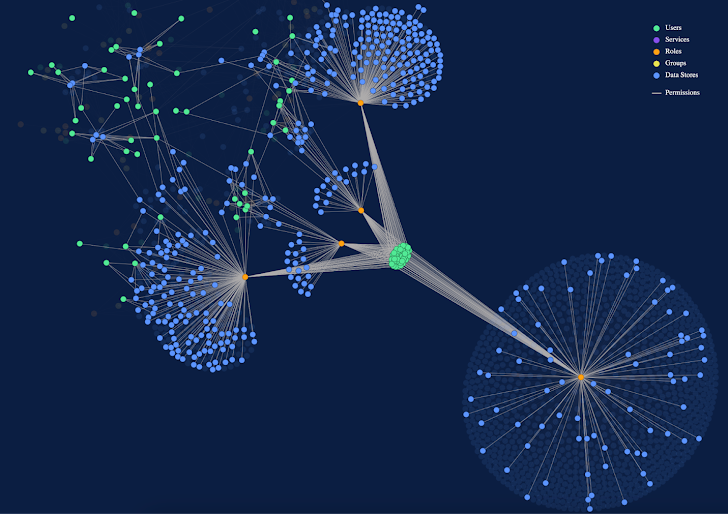
The Importance of Managing Your Data Security Posture
- Jun 15, 2023
Data security is reinventing itself. As new data security posture management solutions come to market, organizations are increasingly recognizing the opportunity to provide evidence-based security that proves how their data is being protected. But what exactly is data security posture, and how do you manage it? Data security posture management (DSPM) became mainstream following the publication […]
Where from, Where to — The Evolution of Network Security
- Jun 14, 2023
For the better part of the 90s and early aughts, the sysadmin handbook said, “Filter your incoming traffic, not everyone is nice out there” (later coined by Gandalf as “You shall not pass“). So CIOs started to supercharge their network fences with every appliance they could get to protect against inbound (aka INGRESS) traffic. In […]
Seven Layers of IT Security
- Jun 14, 2023
Seven Layers Of IT Security Blog Credit: Trupti Thakur Image Courtesy: Google Seven Layers of IT Security What are IT security Layers? IT security layers refer to the several levels of security controls that may be used to defend against online attacks. As we know, there are many other alternatives, but the “defense in […]
Service Set Identifiers in Computer Network
- Jun 13, 2023
Service Set Identifiers In Computer Network Blog Credit: Trupti Thakur Image Courtesy: Google Service Set Identifier (SSID) in Computer Network The primary name for an 802.11 wireless local area network (WLAN), which includes both home networks and public hotspots, is Service Set Identifier (SSID). This name is used by client devices to identify themselves […]
Computer Network Models
- Jun 12, 2023
Computer Network Models Blog Credit: Trupti Thakur Image Courtesy: Google A communication subsystem is a complex piece of Hardware and software. Early attempts for implementing the software for such subsystems were based on a single, complex, unstructured program with many interacting components. The resultant software was very difficult to test and modify. To overcome such […]
5 Reasons Why Access Management is the Key to Securing the Modern Workplace:
- Jun 10, 2023
The way we work has undergone a dramatic transformation in recent years. We now operate within digital ecosystems, where remote work and the reliance on a multitude of digital tools is the norm rather than the exception. This shift – as you likely know from your own life – has led to superhuman levels of […]
Domain Name Server And The Working
- Jun 10, 2023
Domain Name Server- DNS and It’s Working Blog Credit: Trupti Thakur Image Courtesy: Google Domain Name Server is a prominent building block of the Internet. It’s developed as a system to convert alphabetical names into IP addresses, allowing users to access websites and exchange e-mails. DNS is organized into a tree-like infrastructure where the first level […]
Routers In Business Security
- Jun 09, 2023
Routers In Business Security Blog Credit: Trupti Thakur Image Courtesy: Google Overview Routers are essentially “traffic cops” for your small business network. They keep data moving efficiently among multiple network sites as well as to your Internet service provider (ISP), and “translate” different media types and protocols. Different routers serve different types of business […]
How to Improve API Security Posture?
- Jun 09, 2023
APIs, more formally known as application programming interfaces, empower apps and microservices to communicate and share data. However, this level of connectivity doesn’t come without major risks. Hackers can exploit vulnerabilities in APIs to gain unauthorized access to sensitive data or even take control of the entire system. Therefore, it’s essential to have a robust […]
Biometrics In Digital Security
- Jun 08, 2023
Biometrics in Digital Security Blog Credit: Trupti Thakur Image Courtesy: Google What is biometrics? Automatic recognition of people based on their anatomical (e.g., face, fingerprint, iris, retina) and behavioral (e.g., signature, posture) individualities is called Biometrics. It is a form of information that helps in identifying one’s physical characteristics such as psychosomatic, behavioral characteristics, […]
World Environment Day- 2023 #BeatPlasticPollution
- Jun 06, 2023
World Environment Day – 2023 Blog Credit: Trupti Thakur Image Courtesy: Google Theme for the World Environment Day 2023 is under the campaign #BeatPlasticPollution, ‘Ecosystem Restoration’. It is a reminder that people’s action on plastic matters as the material is slowly seeping into our oceans, soil and forest and causing irreparable damage. Fifty […]
Domain Controller- A Security Guard
- Jun 03, 2023
Domain Controller Blog Credit: Trupti Thakur Image Courtesy: Google What Is a Domain Controller? A domain controller is a server computer that authenticates and validates user access on a network. Domain Controller Definition A domain controller is the server responsible for managing network and identity security requests. It acts as a gatekeeper and authenticates whether […]