Digital Personal Data Protection Bill (PDPB), 2023 Gidelines
- Aug 21, 2023
The Digital Personal Data Protection Bill (PDPB) 2023 has been introduced by the Union government in Lok Sabha, aimed at safeguarding personal data and privacy. This comprehensive legislation outlines stringent measures for businesses handling data, individual rights, and the establishment of a regulatory body for enforcement. Let’s delve into the key aspects and implications of […]
First 3D Printed Post Office
- Aug 21, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google India’s First 3D Printed Post Office India’s first 3D printed post office is now open for business in Bengaluru 3D printing technology was adopted to build this building as it saves cost by 30% and time when compared with conventional construction methods The 3D printed post office […]
RBI’s New Guidelines
- Aug 19, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google RBI’s New Guidelines The Reserve Bank of India (RBI) has issued fresh guidelines to Regulated Entities (REs) such as commercial & other banks, NBFCs and other lenders to ensure reasonableness and transparency in disclosure of penal interest. This follows findings that many REs are using penal rates of […]
Zero Shadow Day
- Aug 18, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Zero Shadow Day What is Zero Shadow Day? Zero Shadow Day is a remarkable celestial event that transpires twice a year within locations ranging from +23.5 to -23.5 degrees latitude. During this occurrence, the sun reaches its peak elevation in the sky, causing objects and individuals to cast no […]
Virgin Galactic
- Aug 18, 2023
Virgin Galactic’s VSS Unity, the reusable rocket-powered space plane carrying the company’s first crew of tourists to space, successfully launched and landed on Thursday. The mission, known as Galactic 02, took off shortly after 11am ET from Spaceport America in New Mexico. Aboard the spacecraft were six individuals total – the space plane’s commander and former Nasa astronaut […]
UP’s Tree Plantation Campaign-2k23
- Aug 17, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Tree Plantation Campaign By UP Government 2023. Uttar Pradesh Chief Minister Yogi Adityanath initiated a grand endeavor to plant 5 crore saplings under the Tree Plantation Campaign-2023. Speaking at the inauguration near Gomti bank, he emphasized that safeguarding nature is the key to securing humanity from calamities. […]
ADITYA-L1
- Aug 16, 2023
The Indian Space Research Organisation (ISRO) is launching its first solar mission, Aditya-L1, to study the Sun. The mission will be placed in a halo orbit around the Lagrange point 1 (L1), which is about 1.5 million kilometers from Earth. From this vantage point, Aditya-L1 will be able to study the Sun’s atmosphere, magnetic fields, […]
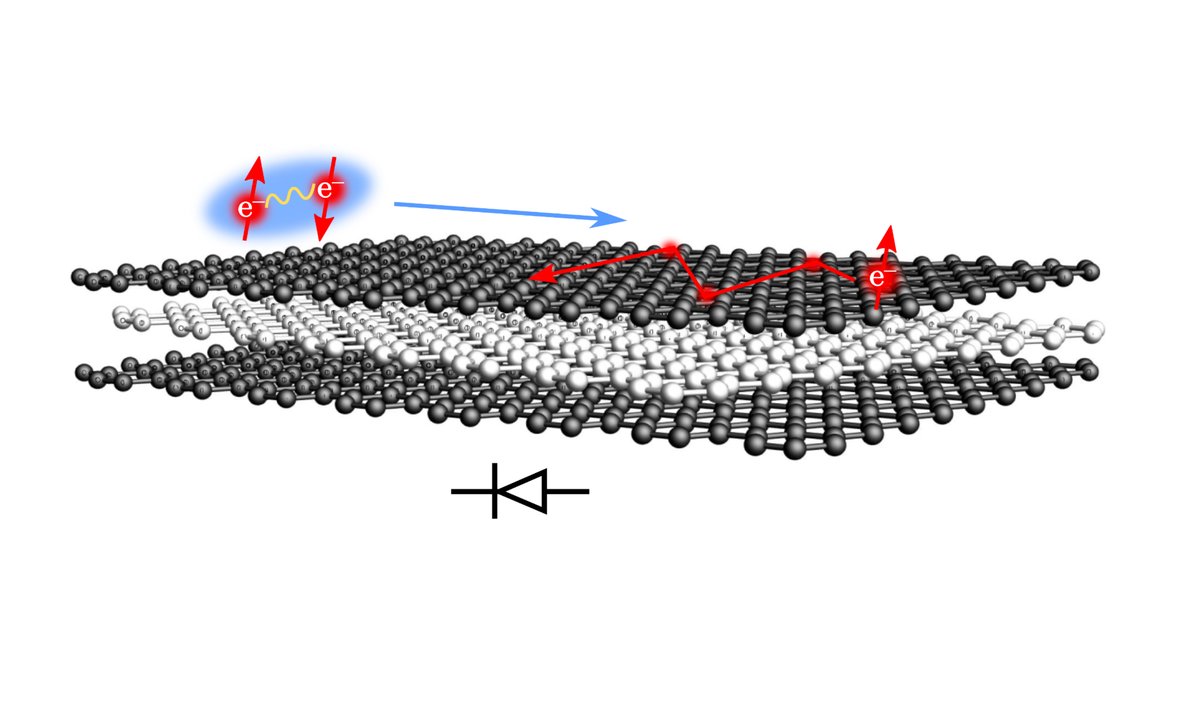
Graphene- Aurora Program
- Aug 16, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Graphene- Aurora Program The Ministry of Electronics & Information Technology (MeitY) Secretary, Shri Alkesh Kumar Sharma, inaugurated the ‘Graphene-Aurora Program’ at Maker Village Kochi, Kerala. The initiative, executed by Digital University Kerala, receives joint funding from MeitY, Government of Kerala, and industry partners, including Carborundum Pvt Limited. […]
How Blockchain and AI can work together?
- Aug 14, 2023
Here, I am going to mention the answer to how Blockchain Technology and Artificial Intelligence can work together! Blockchain and artificial intelligence (AI) are two cutting-edge technologies that have the potential to revolutionize various industries independently. However, when combined, they create a powerful synergy that can drive innovation to new heights. The convergence of blockchain […]
Partition Horrors Remembrance Day
- Aug 14, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Partition Horrors Remembrance Day Partition Horrors Remembrance Day is an annual national memorial day observed on August 14, in India, commemorating the victims and sufferings of people during the 1947 partition of India. The government will observe the Partition Horrors Remembrance Day as the nation gears up to celebrate the […]
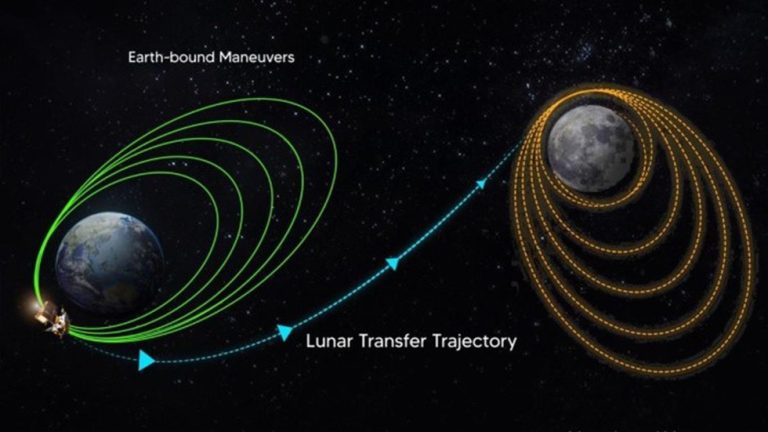
TransLunar Injection
- Aug 11, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Trans-Lunar Injection- TLI The Indian Space Research Organization (ISRO) recently performed the Trans-Lunar Injection (TLI) to slingshot Chandrayaan-3 towards the moon. Trans-Lunar Injection (TLI): A Critical Step in Lunar Missions Trans-Lunar Injection (TLI) is a crucial maneuver in space missions that enables spacecraft to travel from Earth’s […]
Top 8 Trending Technologies To Learn In 2023
- Aug 11, 2023
From cutting-edge technology to cultural shifts, join us as we explore the most fascinating trends that are defining this year. ” AI Takes Center Stage: 2023 is the year of artificial intelligence! AI is everywhere, making our lives easier and more efficient. We’ll explore how smart homes, virtual assistants, and AI-driven healthcare are becoming a […]