Orionid Meteor Shower
- Oct 19, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Orionid Meteor Shower The annual Orionid meteor shower is set to light up the night sky in October 2023. The Orionid Meteor Shower Annual Phenomenon:The Orionid meteor shower occurs every October as Earth passes through the debris left behind by Halley’s Comet, scientifically known as 1P/Halley. Comet Origins:Halley’s […]
Singing Waves Around Mercury
- Oct 18, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Singing Waves Around Mercury Mercury, the smallest planet in our solar system, is often overlooked due to its diminutive size, barely larger than Earth’s Moon. Its proximity to the Sun and the absence of an atmosphere have left its surface pockmarked with countless impact craters. However, recent findings […]
ATMAN Program
- Oct 17, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google ATMAN (Agri sTartup deMo And funding) 2023 Program ATMAN (Agri sTartup deMo And funding) 2023 program was organized by the Department of Science and Technology (DST) in collaboration with four Technology Innovation Hubs. These hubs, established under the National Mission on Inter-disciplinary Cyber-Physical Systems (NM-ICPS) at prominent Indian Institutes of Technology (IITs), played a […]
Watermeal And Space Nutrition
- Oct 16, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Watermeal And Space Nutrition: Watermeal, the world’s tiniest flowering plant, is being studied by researchers at Mahidol University in Thailand as a source of nutrition and oxygen for astronauts. This study used the European Space Agency’s (ESA) Large Diameter Centrifuge (LDC) to submit watermeal to hypergravity conditions at […]
Smart Mobility Conference
- Oct 14, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Smart Mobility Conference Three indigenously developed technologies were introduced at the 11th Traffic Expo and Smart Mobility Conference, furthering India’s progress in various domains. The launch took place in the presence of distinguished officials and experts from the government and the industry. The 11th Traffic Expo and […]
6-G Lab
- Oct 13, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Nokia’s 6-G Lab Telecom giant Nokia has made a significant stride towards the future of wireless technology with the establishment of its state-of-the-art 6G lab at the company’s global R&D center in Bengaluru, India. This “first-of-its-kind” project is set to revolutionize the way we perceive and interact with the digital and physical worlds. […]
“OPERATION AJAY”
- Oct 12, 2023
Blog By: Priyanka Rana “Operation Ajay” Launched to Repatriate Indians from Israel Amidst Tensions India unveiled “Operation Ajay” in response to the escalating conflict triggered by Hamas attacks on Israeli towns, aiming to bring back stranded Indian citizens from Israel. Currently, about 18,000 Indians reside in Israel, according to the Ministry of External Affairs. External […]
‘Asom Mala’
- Oct 12, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Asom Mala In its weekly cabinet meeting, the Assam government has given the green light for a major infrastructure project, the construction of a 1000-kilometer “High-Speed Economic Corridor” road. This ambitious project, with an estimated cost of Rs 3,000 crore, will play a crucial role in enhancing the […]
World Mental Health Day
- Oct 10, 2023
World Mental Health Day Blog By: Priyanka Rana Introduction World Mental Health Day is observed on October 10th every year to raise awareness about mental health issues, reduce the stigma surrounding mental health, and promote overall well-being. In a world where physical health often takes center stage, it’s essential to recognize and prioritize mental health […]
Miura-1
- Oct 10, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Miura-1 Spanish aerospace company PLD Space has achieved a significant milestone by successfully launching its recoverable Miura-1 rocket. This achievement marks Europe’s first fully private rocket launch and offers a glimmer of hope for Europe’s space ambitions. The Miura-1 rocket, named after a fighting bull, conducted a suborbital […]
Psyche
- Oct 09, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Psyche NASA is gearing up for an ambitious mission called Psyche, where a high-tech spacecraft will embark on a 2.2 billion-mile journey to explore an asteroid known as 16 Psyche. This mission, scheduled for launch on October 12, holds immense promise as it aims to delve into the […]
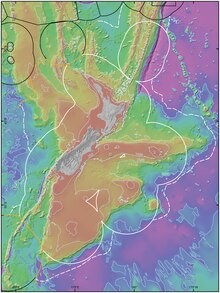
Zealandia
- Oct 07, 2023
Blog Credit: Trupti Thakur Image Courtesy: Google Zealandia A dedicated team of international geologists and seismologists has embarked on a mission to chart the depths of Zealandia, a relatively unknown landmass submerged beneath the Pacific Ocean. Their efforts have resulted in the creation of an updated and highly detailed map that sheds light […]