Software development is the aggregate cycles associated with making programming programs, epitomizing all the phases all through the frameworks improvement life cycle (SDLC).
SDLC systems uphold the plan of programming to meet a business need, the improvement of programming to meet the predefined plan and the organization of programming to creation. A system ought to likewise uphold upkeep, in spite of the fact that that choice might be picked, contingent upon the task being referred to.
Software Development Life Cycle Process
SDLC is a cycle that characterizes the different stages engaged with the improvement of programming for conveying a top-notch item. SDLC stages spread the total life pattern of a product for example from beginning to retirement of the item. Sticking to the SDLC cycle prompts the advancement of the product in a methodical and trained way.
Reason:
The motivation behind SDLC is to convey a great item which is according to the client’s prerequisite.
SDLC has characterized its stages as, Requirement gathering, Designing, Coding, Testing, and Maintenance. It is critical to cling to the stages to give the Product in an efficient way.
For Example, A product must be created and a group is partitioned to chip away at a component of the item and is permitted to function as they need. One of the engineers chooses to plan first though the different chooses to code first and the other on the documentation part.
This will prompt undertaking disappointment due to which it is important to have decent information and comprehension among the colleagues to convey a normal item.
SDLC Cycle
SDLC Cycle represents the process of developing software.
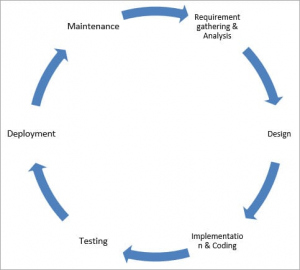
SDLC Phases
Given below are the various phases:
- Requirement gathering and analysis
- Design
- Implementation or coding
- Testing
- Deployment
- Maintenance
1. Requirement Gathering and Analysis
During this stage, all the pertinent data is gathered from the client to build up an item according to their desire. Any ambiguities must be settled in this stage as it were. The business investigator and Project Manager set up a gathering with the client to accumulate all the data like what the client needs to assemble, who will be the end-client, what is the reason for the item. Before building an item a center comprehension or information on the item is significant. For Example, A client needs to have an application that includes cash exchanges. For this situation, the necessity must be away from what sort of exchanges will be done, how it will be done, in which case it will be done, and so forth. When the prerequisite get-together is done, an investigation is done to check the achievability of the advancement of an item. In the event of any equivocalness, a call is set up for additional conversation. When the necessity is perceived, the SRS (Software Requirement Specification) report is made. This report ought to be completely perceived by the designers and ought to be investigated by the client for future reference.
2. Design
In this stage, the prerequisite accumulated in the SRS report is utilized as information, and programming engineering that is utilized for executing framework advancement is inferred.
3. Implementation or Coding
Usage/Coding begins once the designer gets the Design report. The Software configuration is converted into source code. All the parts of the product are executed in this stage.
4. Testing
Testing begins once the coding is finished and the modules are delivered for testing. In this stage, the created programming is tried completely and any deformities discovered are appointed to engineers to get them fixed. Retesting, relapse testing is done until where the product is according to the client’s desire. Analyzers allude to the SRS record to ensure that the product is according to the client’s norm.
5. Deployment
When the item is tried, it is conveyed in the creation condition, or the first UAT (User Acceptance testing) is finished relying upon the client’s desire. On account of UAT, an imitation of the creation condition is made and the client alongside the designers does the testing. In the event that the client finds the application true to form, at that point close down is given by the client to go live.
6. Maintenance
After the organization of an item on the creation condition, upkeep of the item for example in the event that any issue comes up and should be fixed or any improvement is to be done is dealt with by the engineers.
Programming Development Life Cycle Models
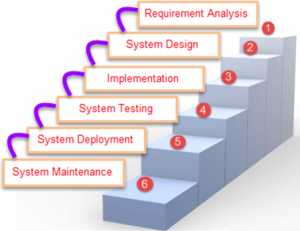
Waterfall Model
The cascade model is the absolute first model that is utilized in SDLC. It is otherwise called the direct successive model. In this model, the result of one stage is the contribution of the following stage. The advancement of the following stage begins just when the last stage is finished.
1. To begin with, Requirement social event and examination are finished. When the necessity is freeze then just the System Design can begin. In this, the SRS record made is the yield for the Requirement stage and it goes about as a contribution for the System Design.
2. In System Design Software engineering and Design, records that go about as a contribution for the following stage are made for example Execution and coding.
3. In the Implementation stage, coding is done and the product created is the contribution to the following stage for example testing.
4. In the testing stage, the created code is tried all together to distinguish the imperfections in the product. Deformities are signed into the imperfection following the instrument and are retested once fixed. Bug logging, Retest, Regression testing goes on until the time the product is in go-live state.
5. In the Deployment stage, the formed code is moved into creation after the closedown is given by the client.
6. Any issues in the creation condition are settled by the designers which go under upkeep.
Advantages of the Waterfall Model:
Lately, the Waterfall model has given its driving situation to more adaptable philosophies. This is because of the overall changes in IT, where the cutoff time can be handily moved because of the usefulness of the turn of events.
Nonetheless, the Waterfall model is as yet utilized as it gives the accompanying advantages:
1. The prerequisites are unmistakably and precisely expressed, they stay unaltered all through the whole venture improvement;
2. Definite documentation of every improvement stage gives protection from changes in HR – another engineer can rapidly get all the vital data;
3. Cautious arranging of the venture improvement structure diminishes the quantity of dangerous issues;
4. The beginning and end focuses for each stage are set, which gains it simple to quantify ground;
5. The errands stay as steady as conceivable all through the improvement cycle;
6. It gives simple control and straightforwardness to the client because of an exacting announcing framework;
7. Delivery date for the completed item, just as its last expense can be determined before advancement.
The Disadvantages of the Waterfall Model
Tragically, there isn’t anything ideal in our reality, which is the reason the Waterfall strategy has clear shortcomings:
1. All prerequisites must be known before improvement, which significantly postpones the task the opening shot;
2. Low adaptability level makes it hard to make changes while creating, or even makes it totally inconceivable;
3. There is a requirement for severe administration and ordinary observing, with the goal that the task will fulfill the time constraint;
4. The customer doesn’t have the chance to get to know the framework ahead of time, so he doesn’t see the item until the snapshot of its finishing;
5. In the event that it turns out to be clear during the time spent improvement that the item doesn’t meet market necessities, there will be no space for changes.
All in all, when utilizing Waterfall, it is practically difficult to return to a past stage and fix something. In the event that a specific stage has been finished, however with blunders, the following stages will likewise be compromised.
V-Shaped Model
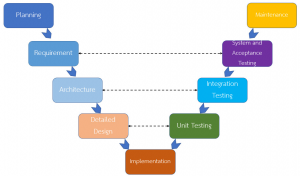
V-Model is otherwise called Verification and Validation Model. In this model Verification and Validation goes connected at the hip for example advancement and testing goes equal. V model and cascade model are the equivalent aside from that the test arranging and testing start at a beginning phase in V-Model.
Prototype Model
The prototype is a model wherein the model is created preceding the genuine programming. Prototype models have restricted practical abilities and wasteful execution when contrasted with the real programming. Sham capacities are utilized to make models. This is an important instrument for understanding the clients’ needs.
Software prototypes are worked preceding the real programming to get important criticism from the client. Criticisms are actualized and the model is again looked into by the client for any change. This cycle goes on until the model is acknowledged by the client.
When the necessity gathering is done, the speedy plan is made and the model which is introduced to the client for assessment is constructed.
Client input and the refined necessity is utilized to alter the model and is again introduced to the client for assessment. When the client supports the model, it is utilized as a prerequisite for building the genuine programming. The genuine programming is fabricate utilizing the Waterfall model methodology.
Focal points of Prototype Model:
1. The model lessens the expense and season of advancement as the deformities are discovered a lot before.
2. Missing highlights or usefulness or an adjustment in prerequisite can be recognized in the assessment stage and can be actualized in the refined model.
3. The contribution of a client from the underlying stage diminishes any disarray in the necessity or comprehension of any usefulness.
Hindrances of Prototype Model:
1. Since the client is associated with each stage, the client can change the necessity of the finished result which expands the intricacy of the degree and may build the conveyance season of the item.
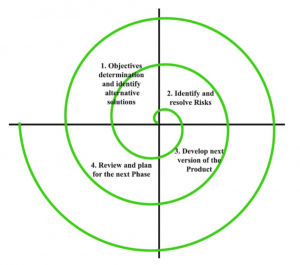
Spiral Model
The Spiral Model incorporates iterative and model methodology.
Winding model stages are followed in the cycles. The circles in the model speak to the period of the SDLC cycle for example the deepest circle is of prerequisite social event and examination which follows the Planning, Risk investigation, improvement, and assessment. The following circle is Designing trailed by Implementation and then testing.
Winding Model has four stages:
- 1 Planning
- 2 Risk Analysis
- 3 Engineering
- 4 Evaluation
(I) Planning:
The arranging stage incorporates necessity gathering where all the necessary data is accumulated from the client and is recorded. Programming necessity detail archive is made for the following stage.
(ii) Risk Analysis:
In this stage, the best arrangement is chosen for the dangers in question, and the investigation is finished by building the model.
For Example, the danger associated with getting to the information from a distant information base can be that the information access rate may be excessively moderate. The danger can be settled by building a model of the information access subsystem.
(iii) Engineering:
When the danger examination is done, coding and testing are finished.
(iv) Evaluation:
The client assesses the created framework and plans for the following cycle.
Iterative Incremental Model
The iterative gradual model partitions the item into little pieces.
For Example, Feature to be created in the emphasis is chosen and actualized. Every cycle experiences the stages in particular Requirement Analysis, Designing, Coding, and Testing. Point by point arranging isn’t needed in cycles.
When the emphasis is finished, an item is confirmed and is conveyed to the client for their assessment and input. Client’s criticism is actualized in the following cycle alongside the recently included element.
Thus, the item increases regarding highlights and once the cycles are finished the last form holds all the highlights of the item.
Periods of Iterative and Incremental Development Model:
- 1 Inception stage
- 2 Elaboration Phase
- 3 Construction Phase
- 4 Transition Phase
(I) Inception Phase:
Commencement stage incorporates the necessity and extent of the Project.
(ii) Elaboration Phase:
In the elaboration stage, the working engineering of an item is conveyed which covers the danger recognized in the origin stage and furthermore satisfies the non-utilitarian necessities.
(iii) Construction Phase:
In the Construction stage, the engineering is filled in with the code which is fit to be conveyed and is made through examination, planning, usage, and testing of the utilitarian necessity.
(iv) Transition Phase:
In the Transition Phase, the item is conveyed in the Production condition.
Focal points of Iterative and Incremental Model:
1 Any adjustment in the prerequisite can be effortlessly done and would not cost as there is an extent of joining the new necessity in the following emphasis.
2 Risk is investigated and recognized in the cycles.
3 Deformities are distinguished at a beginning phase.
4 As the item is separated into littler lumps it is anything but difficult to deal with the item.
Inconveniences of Iterative and Incremental Model:
1 Complete necessity and comprehension of an item are needed to separate and assemble gradually.
Enormous detonation Model
Enormous detonation Model doesn’t have any characterized cycle. Cash and endeavors are assembled as the info and yield come as a created item which may be or probably won’t be equivalent to what the client needs.
Enormous detonation Model doesn’t need a lot of arranging and planning. The engineer does the necessity examination and coding and builds up the item according to his comprehension. This model is utilized for little ventures as it were. There is no trying group and no proper testing is done, and this could be a reason for the disappointment of the task.
Inconveniences of Iterative and Incremental Model:
1 It’s an exceptionally basic Model.
2 Less Planning and booking is required.
3 The designer has the adaptability to assemble the product of their own.
Inconveniences of Iterative and Incremental Model:
1 Big Bang models can’t be utilized for huge, progressing and complex activities.
2 High danger and vulnerability.
Agile Model
The Agile model is a blend of the Iterative and gradual model. This model zeros in additional on adaptability while building up an item instead of on the necessity.
In Agile, an item is broken into little gradual forms. It isn’t created as a total item in one go. Each form increases regarding highlights. The following form is based on past usefulness.
In coordinated emphases are named as runs. Each run endures for 2 a month. Toward the finish of each run, the item proprietor checks the item and after his endorsement, it is conveyed to the client.
Client input is taken for development and his recommendations and improvement are dealt with in the following run. Testing is done in each run to limit the danger of any disappointments.
Conclusion
Adherence to a reasonable life cycle is significant, for the effective finish of the Project. This, thusly, makes the administration simpler.
Diverse Software Development Life Cycle models have their Pros and Cons. The best model for any Project can be dictated by the variables like Requirement (regardless of whether it is clear or muddled), System Complexity, Size of the Project, Cost, Skill restriction, and so forth.
Model, in the event of an indistinct necessity, Spiral and Agile models are ideal to be utilized as the necessary change can be obliged effectively at any stage.
Cascade model is a fundamental model and the various SDLC models depend on that as it were.
Get started


